
Five of them allow remote compromise of the IoT gadgets, so attackers can intercept video feeds and more.

Fog computing for next-generation Internet of Things: Fundamental, state-of-the-art and research challenges - ScienceDirect
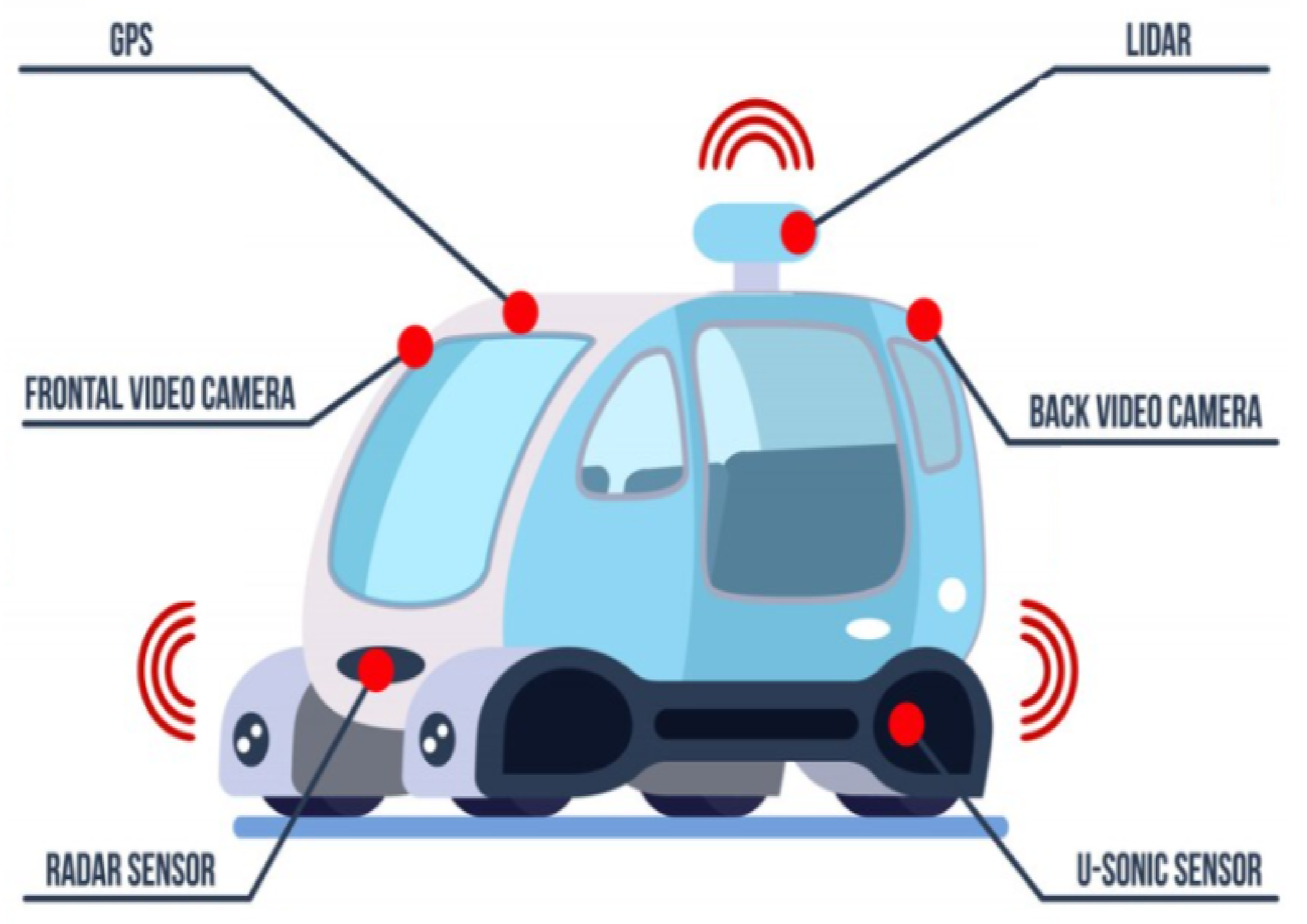
Sensors, Free Full-Text
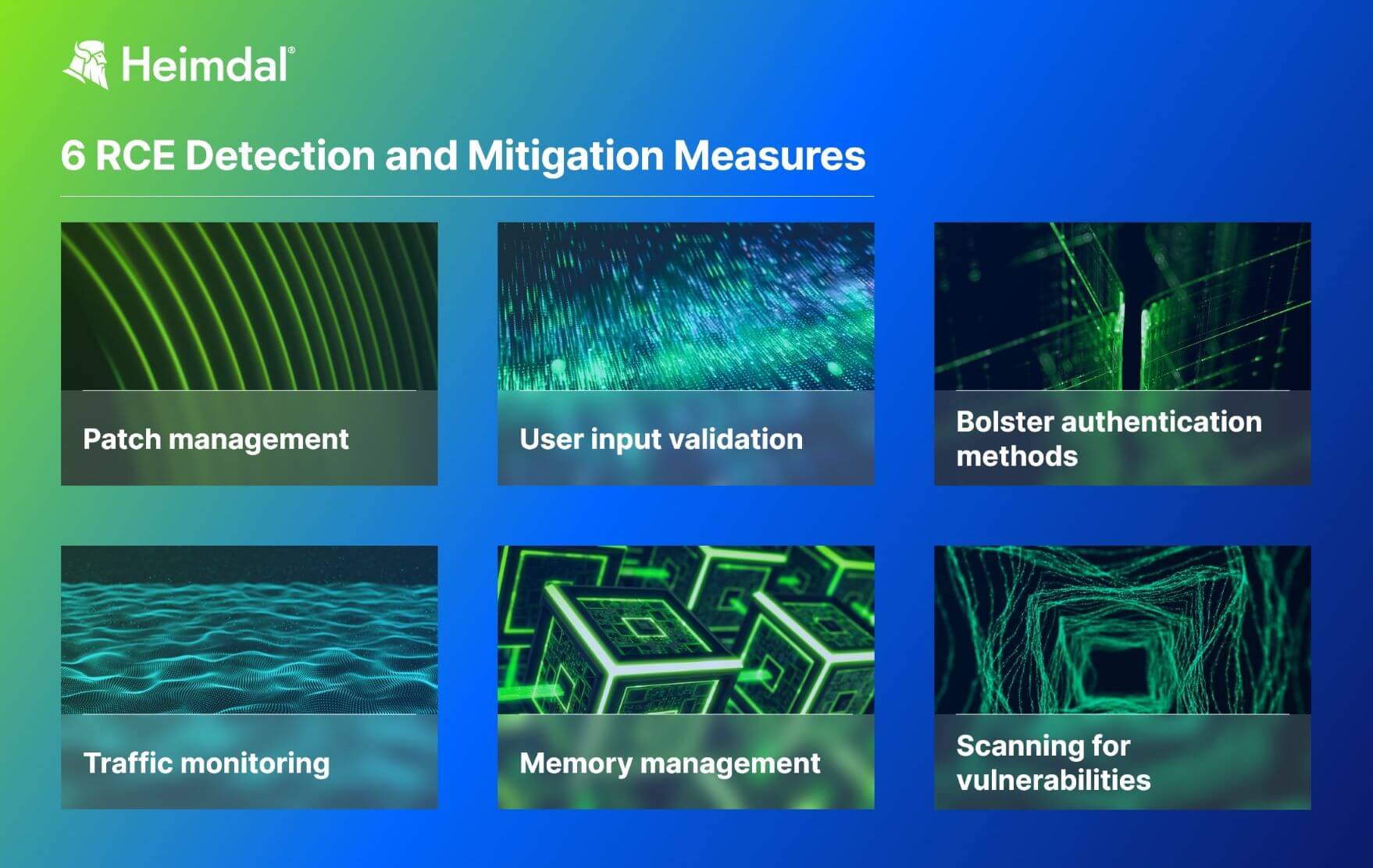
What Is a Remote Code Execution Attack? Definition, Risks, and Mitigation Measures

PortSwigger — LAB-6 Remote code execution via polyglot web shell upload (Bug Bounty Prep)[by dollarboysushil], by dollarboysushil, Feb, 2024

YiToo WiFi Tuya Access Control Fail-Safe Electric Strike Door Lock Kit System Gate Remote Control Opener Smartphone APP Control

A systematic review of the purposes of Blockchain and fog computing integration: classification and open issues, Journal of Cloud Computing

Zero Day Initiative — Riding the InfoRail to Exploit Ivanti Avalanche

Office and Windows HTML Remote Code Execution Vulnerability

Popular IoT Cameras Need Patching to Fend Off Catastrophic Attacks
.png)
Cyber Hygiene: Ransomware is Causing Critical Care Disruption in Hospitals - Securin
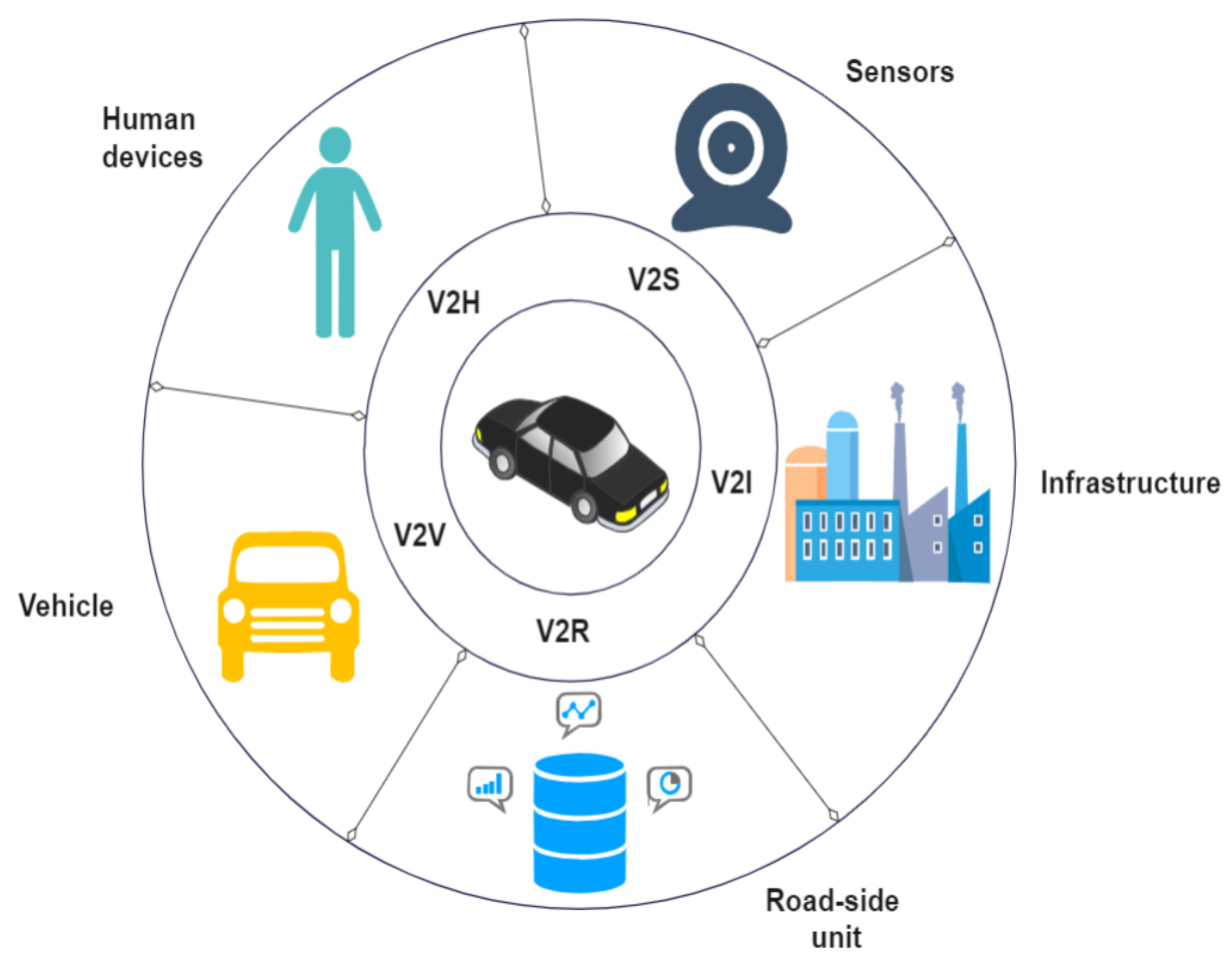
Sensors, Free Full-Text






